Data breaches can immediately impact hundreds of millions or possibly billions of individuals in the data-driven world today. Data breaches have grown in scope along with digital transformation as attackers take advantage of our everyday reliance on data.
Although it is impossible to predict how big cyberattacks may get in the future, this list of the biggest data breaches from the twenty-first century shows that they have already gotten ridiculously huge.
Examples of data breaches and their impact
Data breaches can be far more than a temporary terror. They may change the course of your life or your business. Businesses, governments, and individuals alike can experience huge complications from having sensitive information exposed. Whether you are offline or online, hackers can get to you through the internet, Bluetooth, text messages, or the online services that you use.
Intentional attacks can occasionally be linked to the causes of data leaks. It may, however, also be the result of a person’s carelessness or weaknesses in the infrastructure of a business.
Here is an example of a data breach:
- An insider by accident. An illustration would be a worker viewing files on a coworker’s computer without the necessary authorization permissions. There is no information disclosed and the access is accidental. However, the data is regarded as compromised because it was read by an uninvited party.
- Lost or stolen devices. An unencrypted and unlocked laptop or external hard drive — anything that contains sensitive information — goes missing.
- Malicious outside criminals. “These are hackers who use various attack vectors to gather information from a network or an individual.”
- A malicious insider: With the intention of hurting a person or business, this person willfully accesses and/or discloses data. “The malicious insider may have legitimate authorization to use the data, but the intent is to use the information in nefarious ways.” (“What is a Data Breach & How to Prevent One – Kaspersky”)
Listen to the challenges of Data Analysis in cyber security
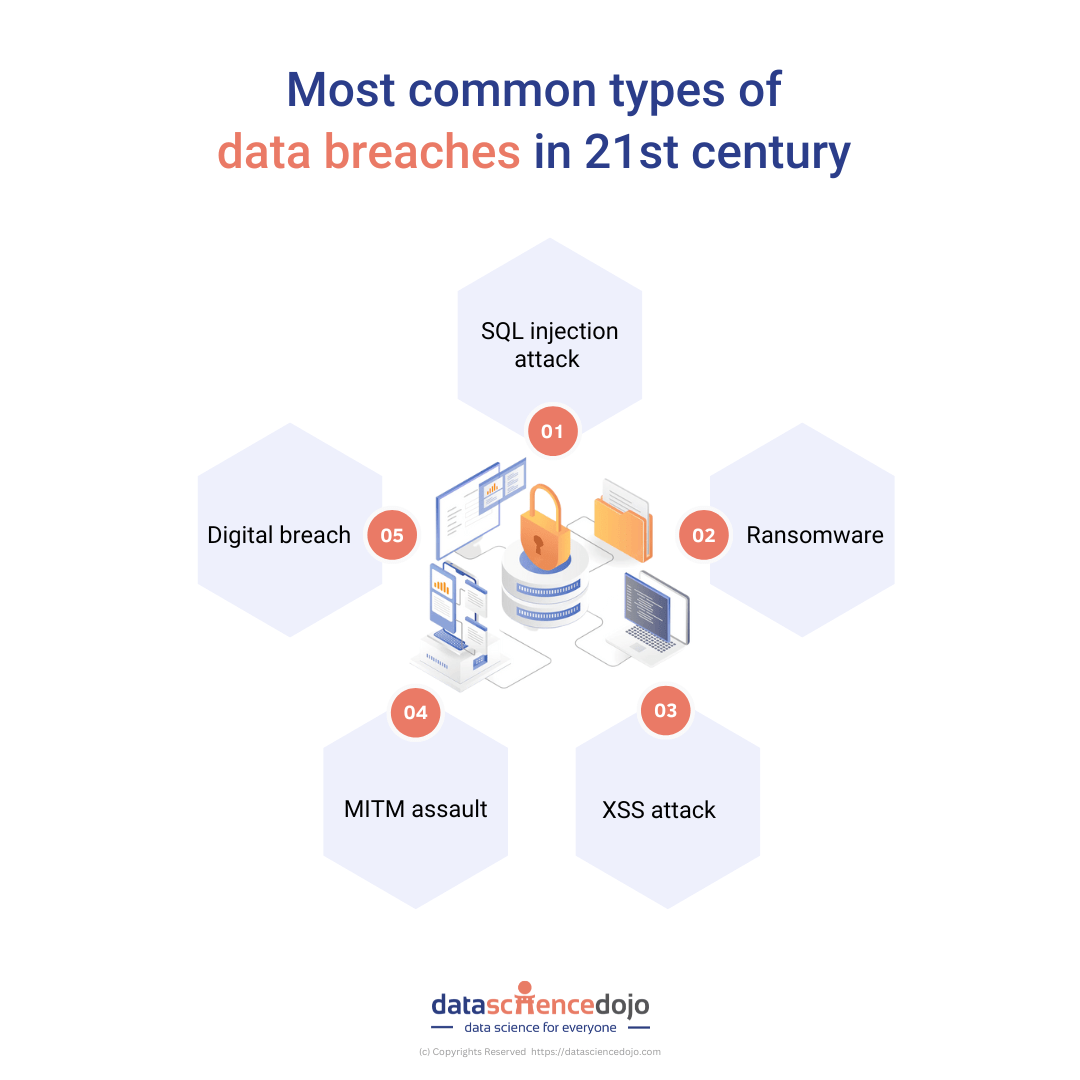
Most common types of data breaches in 21st century
1. SQL Injection attack
Similar to XSS assaults, a SQL Injection attack inserts malicious code into the system, but often SQL rather than HTML. In a SQL Injection attack, malicious code from the attacker accesses a system via a database.
Although a lot of online apps employ databases as trustworthy third parties, it is crucial to make sure that no unauthorized parties are receiving data. Anyone with access to the database can steal information or carry out a SQL Injection attack to steal cash or other assets.
2. Ransomware
An unexpected notification informing you that your computer or phone has been compromised is known as ransomware. In this situation, the individual will inform you that if you pay a charge, they will provide it to you in exchange for keeping it private. This might range from being negligible to costing hundreds of thousands of dollars.
In order to prevent the leak or deletion of crucial or compromising materials, many businesses work with risk management solution providers.
3. XSS attack
Web applications that exploit common vulnerabilities like XSS vulnerabilities may be exposed to cross-site scripting (XSS) attacks, a remote code execution (RCE) issue. When a remote attacker transmits malicious code to a web application, RCE problems can develop.
Because the malicious code switches the web app’s execution to a script that could be anywhere on a computer network or even on other computers in the network, XSS vulnerabilities are usually simple to identify.
4. MITM assault
A man-in-the-middle (MITM) attack occurs when a perpetrator intercepts and steals data from a computer or network while posing as a third party. An attacker could, for instance, be present at a workplace, a hotel room, or a storage location when data is being seen by a computer user.
The most frequent risk of MITM attacks is the public disclosure of sensitive data such as names, email addresses, dates of birth, financial information, health information, and other data.
5. Digital breach
A system or network environment where cardholder data is processed, stored, or sent is subject to an electronic breach if someone gains unauthorized access to it or deliberately attacks it.
This could happen because of application-level assaults finding a system’s weaknesses via web servers or webpages.
For instance, the healthcare sector is frequently impacted by data breaches since access to these networks exposes a lot of confidential patient credit card information.
Major data breaches across the world
Some of the major data breaches that took place across the world
Recently, major corporations have suffered data loss due to hacking and incidents of data breaches. Some of the most renowned of these are:
1. Canva:
The namesake graphic design service, Canva, a Sydney-based business, was breached 2019, according to ZDNet. According to the hacker who alerted ZDNet, the incident resulted in the theft of data for almost 139 million customers. The compromise was caused by a hacker using the alias GnosticPlayers online. The hacker is well-known. He/she/they have been selling the 932 million user records that they acquired from 44 international businesses since 2019 February on the dark web.
2. Shanghai National Police (SHGA):
The Shanghai National Police (SHGA) database was infiltrated in 2022. Major crucial data and information about billions of Chinese residents are contained in this database. The lot was being sold by HackerDan for 10 Bitcoin.
3. Facebook:
Several online vulnerable databases were found to include 419 million records of Facebook users, dealing a fatal blow to over 20% of Facebook’s 2.3 billion users, according to TechCrunch. The records were kept on a server and were not password-protected, so anyone with an internet service could freely retrieve them.
4. Microsoft:
250 million Microsoft customer records from 14 years ago have been exposed online without data encryption, according to a recent investigation. Recently, Microsoft has primarily been featured for different purposes in the headlines. Despite being frequently exploited, Microsoft has not released a patch for the Internet Explorer zero-day vulnerability.
5. LinkedIn:
In June 2021, the dark web forum hosting 700 million LinkedIn users’ data was leaked, affecting more than 90% of the company’s user base. By abusing the site’s API, a hacker going by the handle “God User” used data scraping techniques before leaking the first private set of data of approximately 500 million users.
Protect yourself from data breaches
You must take the necessary steps to protect data and your confidential documents and electronic media in order to safeguard yourself from becoming a victim of a data breach, whether the perpetrator is a dumpster-diving identity thief looking for your discarded medical bills or a hacker who is targeting the network of your business in order to steal customer information.
References:
What is a Data Breach & How to Prevent One – Kaspersky

