In order for businesses to respond to SaaS threats efficiently and adhere to industry requirements, SSPM (SaaS security posture management) poses a vital component. But to safeguard SaaS access, SSPM is frequently insufficient, unfinished, and ineffectual.
The Explanation of SSPM (SaaS Security Posture Management)
Businesses are increasingly embracing SaaS software to manage a variety of operations, including marketing and sales. The myriad concerns it raises for compliance and security increase as this tendency skyrockets at the same time. SaaS app usage oversight is possible with the help of SSPM. Let’s describe SSPM. The phrase describes the tools used by companies to identify, evaluate, and lower these risks.
SaaS apps may expose users to the following threats:
- Issues with compliance
- Lax rules for permitted use
- Unstable settings
- Potentially still-accessible inactive users
SSPM security gives businesses the power they need to safeguard important corporate information that resides across many apps, as well as sometimes personal information.
Whether it’s a straightforward blog page or a complex e-commerce website, cybercriminals are continuously searching for new ways to harvest data from web pages and web apps. Any company’s website security, as well as subscribers’ info (many membership websites must collect recurring payments and establish several levels of member access), depends on the third-party service providers it uses.
All in all, SSPM security provides insights into prospective SaaS issues that your teams could run into, allowing you to look for ways to avoid problems.
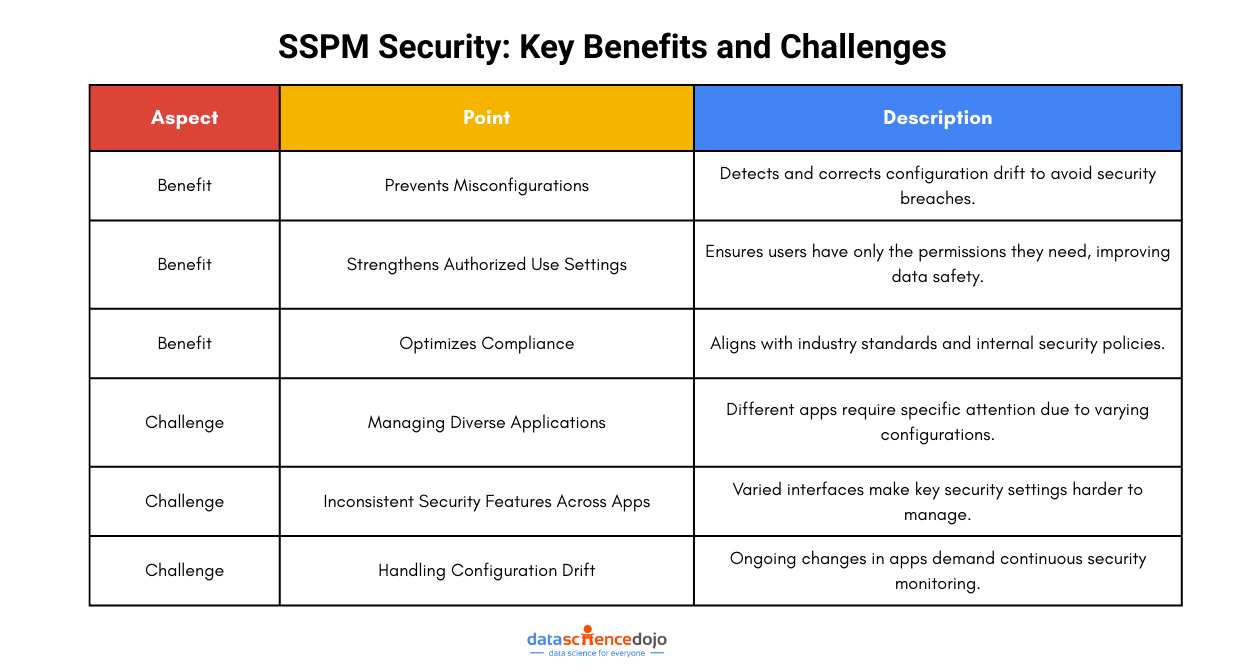
Benefits of SSPM Security
Businesses may experience serious security and regulatory repercussions if SaaS application security posture management isn’t implemented. The benefits listed below show why SSPM is essential for many organizations.
Measures to Prevent Misconfigurations
Misconfigurations provide the most significant risk to cloud security and are a factor in a large number of data breaches. Even if an app is first configured correctly by a company, later compliance issues could arise from subtle deviations.
A company can more easily maintain safe configurations with the help of SSPM, even if apps change and clients who use them alter.
Makes Authorized Use Settings more Robust
Not every worker will have access to the same information, even inside a single app. If users have additional permissions in an app than they have been granted, SSPM looks at the resources to find out.
By ensuring that only individuals who are authorized can access and modify the data, this feature improves data security.
Optimizes Compliance
SaaS solutions have increased the complexity of compliance management. By constantly comparing safety practices with internal frameworks and industry standards, SSPM overcomes these difficulties.
Despite the significant advantages of SSPM, posture management may be a very challenging procedure for both small and large businesses. As a result, SSPM security faces a number of difficulties, such as:
- Managing a variety of apps: Configuration, data transfer, and other similar tasks may be approached differently by various apps. Effective security requires the time-consuming effort of going over each one.
- Finding security features in each configuration requires businesses to navigate a variety of app interfaces, and these features may appear differently in each app. Simple operations, like allowing staff to use specific apps, could become ineffective as a result.
- Taking action in the face of configuration drift: Setting up an app just once rarely suffices because it can deviate from the original configuration, opening the door for security issues if left unchecked.
Why SSPM Is Insufficient?
Even though SSPM may be helpful for businesses, it’s an inadequate security strategy since it ignores the ever-changing character of SaaS systems. Administrators can only find issues with SSPM when certain settings are met. They are not given any assistance in figuring out who utilizes these apps or how they are used.
Furthermore, only a few applications, including Slack, Microsoft Office 365, and Salesforce are frequently supported by SSPM systems. Because of this, businesses find it challenging to rely entirely on SSPM for SaaS resources.
SaaS Security Control Plane (SSCP) Usage
Mixing the aforementioned solution with a SaaS Security Control Plane (SSCP) may be advantageous for businesses that have solely adopted SSPM security. The SSCP must be implemented by any business that wants to protect itself against the security hazards of the modern world. Utilizing security rules for people and processes, it scans the entire SaaS architecture for hazards.
Additionally, SSCP covers a wider range of SaaS resources, including managed and unmanaged devices as well as sanctioned and unsanctioned apps. SCCP is extremely effective and has a quick deployment time.
SSPM vs. SSCP
The SSCP involves setting up security throughout the entire infrastructure, as was already mentioned. This covers people, processes, and apps, in addition to technology like SSPM. It goes above and beyond the typical safeguards for widely used applications like Office 365 to keep track of all the resources a company utilizes on a regular basis.
An SSCP’s improved capabilities enable your company to freely use apps with the knowledge that they are all secure. Additionally, it may reduce the risks that SSPM introduces when managing divergent configurations across various apps, including drift and any ensuing compliance issues. Employing SSCP in this way helps you uphold industry requirements while also enhancing your security plan.
A New Solution Emerged: CSPM
It’s crucial to assess SSPM solutions’ potential as they gain popularity in the security industry. This kind of activity is especially necessary right now since cybersecurity threats are growing and IT funds are under review.
After all, CSPM’s (Cloud Security Posture Management’s) capacity to spot cloud network errors and safeguard your data housed in Azure, Google Cloud, AWS, and other cloud hosting alternatives can’t be replaced by SSPM. The usefulness of CSPM’s risk assessment and mitigation for enterprises with just cloud-based data storage is undeniable. But what about the information you have stored elsewhere? And all the settings in the dozens, if not hundreds, of SaaS apps that your company uses every day?
These malware and data loss scenarios aren’t just for a cocktail party. The number of high-profile security incidents and breaches involving providers and third-party vendors continues to rise.
The CSPM is ill-prepared to deal with evolving cybersecurity risks. You need a distinct security posture to address the SaaS application vulnerabilities, especially those that store sensitive data.
What’s the Purpose of CSPM’s Monitoring and Why Isn’t SaaS Data Protected?
Vendors of CSPM software keep track of the compliance and security status of both generic and specific cloud apps that are installed in public cloud environments. Additionally, they frequently offer DevOps, dynamic cloud integration, and compliance monitoring capability.
The SaaS applications’ security posture and associated data, which is frequently the most sensitive data for a corporation, is neglected when relying just on CSPM. Because of this, enterprise applications like Microsoft 365, ServiceNow, and Salesforce are vulnerable to dangerous structures, configuration drift, and non-compliance. Additionally, the thousands of SaaS programs utilized by organizational divisions and departments make security breaches even more likely.
How Can SaaS Security Vulnerabilities Be Mitigated by SSPM?
In SaaS applications, data security is the main focus of SSPM. It swiftly and automatically identifies app misconfigurations and associated security flaws.
Of all, SaaS’s much-lauded adaptability is precisely what exposes businesses to a variety of security flaws and incorrect configurations. Even with security guidelines in place, modifications made in business settings are frequently not communicated to security and IT teams.
Although it may appear to be unimportant from the viewpoint of a user or business owner, this unmonitored and undetected behavior might lead to security flaws and insecure SaaS data.
With SSPM in place, you’ll be able to stop potentially detrimental changes by knowing what changes staff members are making to apps. Your company will be able to monitor cloud-based SaaS apps like Microsoft 365, ServiceNow, Salesforce, and others automatically and continuously.
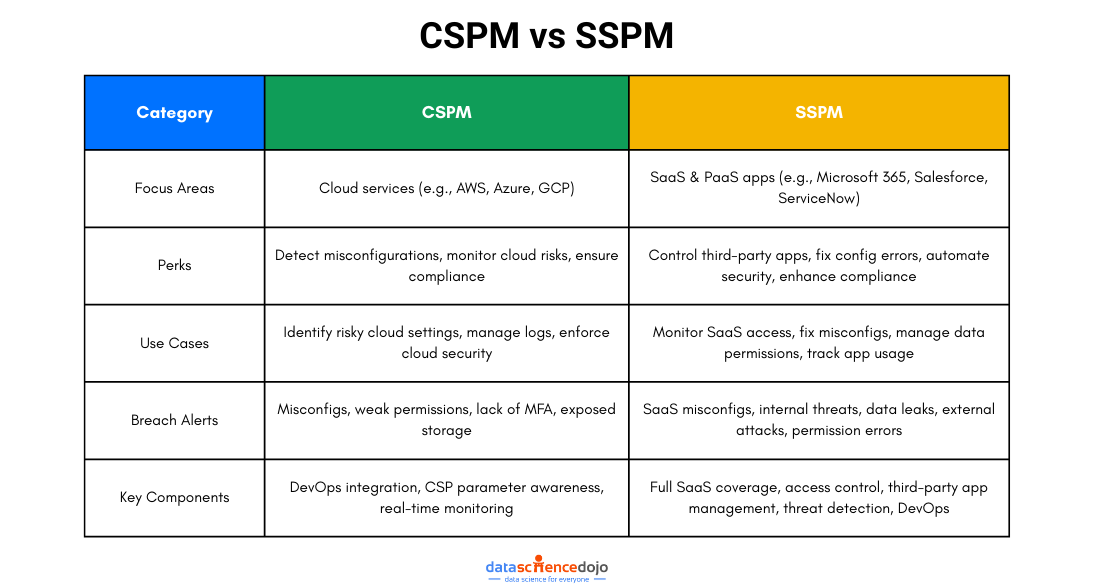
Without increasing their workloads, your security team can help ensure compliance by identifying overly permissive settings. SSPM vs. CSPM
|
CSPM |
SSPM |
|
| Focus areas | Watching over cloud services like Azure, Cloud, and AWS. | Watch over SaaS and PaaS programs like ServiceNow, Microsoft 365, and Salesforce, among others. Some solutions additionally protect unique applications. |
| Perks |
|
|
| Cases of use |
|
|
| Security breach alerts |
|
|
| Key components |
|
|
Is SSPM Investment Worthwhile?
Without an SSPM tool, your company will be forced to:
- Count on each application to protect itself. The monitoring performed by the native security tool will also be impacted if that application is ever compromised.
- Limit security analysis and monitoring scope to native app features. Your staff will waste time monitoring dozens, and often even hundreds, of security dashboards that frequently fail to keep track of the numerous integrations that users have added. The workloads for the security team frequently increase in complexity and demand more resources.
CISOs, CIOs, and the sector at large are now more aware of these historical security flaws. According to Gartner’s 2022 Application Security Hype Cycle, SSPM is very advantageous to businesses. Additionally, the expense and harm to one’s reputation caused by a SaaS data event much outweigh anything invested in a SaaS-focused security posture.
Do You Need SSPM, CSPM, or Both for Your Organization?
For businesses with complex tech stacks spanning multiple cloud providers and third-party applications, preventing security risks like configuration drift is critical. SSPM (Security Service Posture Management) and CSPM (Cloud Security Posture Management) provide essential solutions to safeguard data.
SSPM enhances security teams’ efficiency by automating the protection of data across platforms, while CSPM ensures real-time monitoring and protection of cloud environments. By integrating these tools, businesses can strengthen their security posture, maintain compliance, and prevent data breaches in an increasingly complex digital landscape.
Written by Mahendra Bajiya